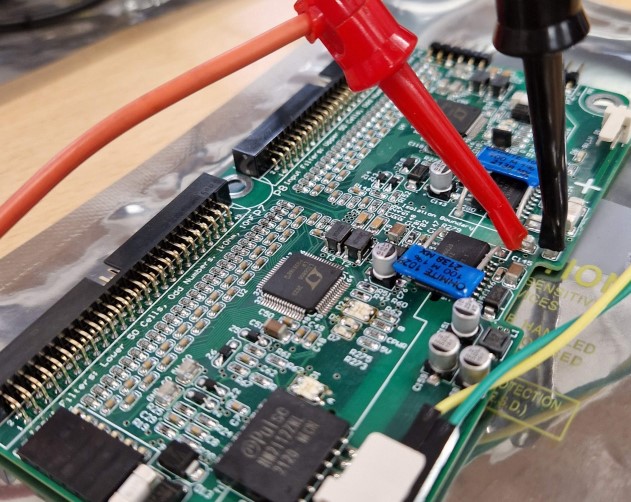
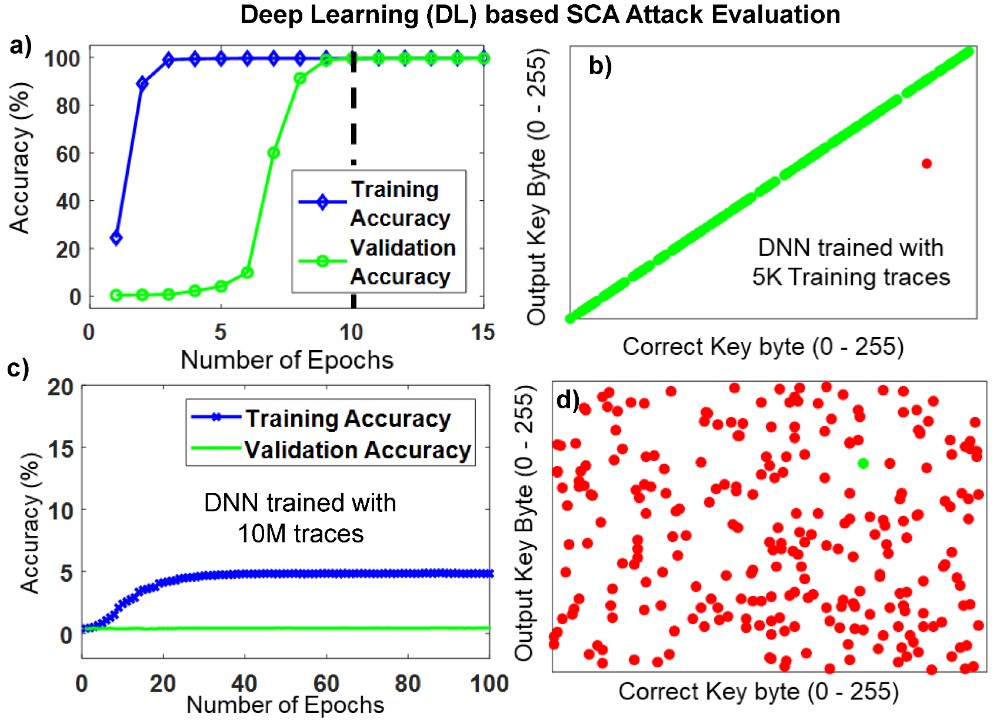
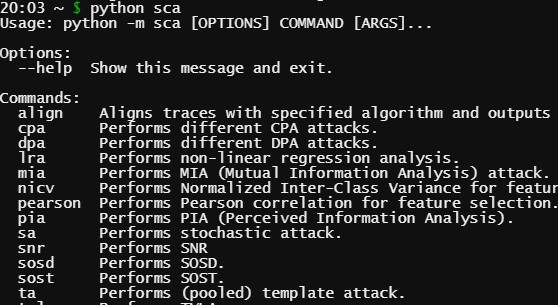
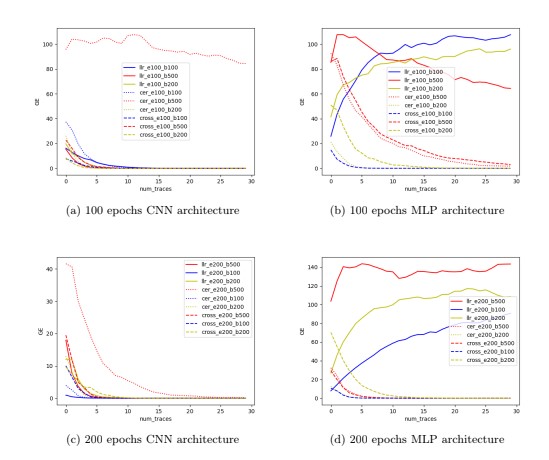
I have done many different projects within the field of Side-Channel Analysis (SCA), my MSc Thesis even dug deeper into the subject and made a major improvement to the field. To showcase some of these projects I have made this collection, please see the project previews above, they are in chronological order.
If you’re not familiar with the field, I would suggest reading the description of SCA and its developments below.
What is it?
Side-channel analysis (SCA) is a class of attacks that aim to extract sensitive information from a target system by analyzing unintended side-channel information that is leaked during its operation. Unlike traditional attacks that focus on exploiting software vulnerabilities, SCA targets the physical implementation of a system, taking advantage of the unintentional information leaks that occur through various physical channels.
The basic idea behind side-channel analysis is that when a system performs cryptographic operations or other sensitive computations, it consumes power, emits electromagnetic radiation, produces acoustic noise, or exhibits other observable behaviors that are correlated with the operations being performed. These side channels provide valuable information that can be exploited to infer secret data, such as encryption keys or intermediate computations.
To mitigate side-channel attacks, various countermeasures can be employed during the design and implementation of systems. These include techniques such as power and timing masking, randomizing operations, and incorporating noise to hide the side-channel leakage.
Overall, side-channel analysis is a powerful technique that attackers can use to exploit physical information leakage and extract sensitive data from a target system. Therefore, it is crucial for designers and developers to be aware of side-channel vulnerabilities and implement appropriate countermeasures to enhance the security of their systems.
How can this be done?
There are several types of side-channel attacks, each focusing on a different physical channel:
Power Analysis: This attack involves analyzing the power consumption of a device during cryptographic operations. By measuring and analyzing the power consumption variations, an attacker can deduce information about the internal computations, such as key bits or intermediate values.
Timing Analysis: Timing attacks exploit variations in the execution time of cryptographic operations to gain information about secret data. By measuring the time taken for different operations or analyzing the timing patterns, an attacker can deduce information about the data being processed.
Electromagnetic Analysis: Electromagnetic emissions from a device can provide information about the internal operations. By analyzing the electromagnetic radiation emitted during cryptographic operations, an attacker can extract sensitive data.
Acoustic Analysis: Some devices produce acoustic noise during their operations. By analyzing the acoustic signals, an attacker can gain insights into the computations being performed.
Fault Analysis: Fault attacks involve intentionally inducing faults in a device’s operation and observing the effects. By carefully manipulating the device, an attacker can induce faults that reveal secret information or bypass security mechanisms.
AI in the field
The development of deep learning and AI methods has played a significant role in improving the field of side-channel analysis. Here are some key advancements, in chronological order:
Neural Networks for Side-Channel Analysis: Deep learning techniques, particularly neural networks, have been successfully applied to side-channel analysis tasks. Neural networks can learn complex patterns and correlations in side-channel data, enabling them to perform efficient and accurate analysis. Researchers have developed neural network architectures, such as convolutional neural networks (CNNs) and recurrent neural networks (RNNs), tailored for side-channel analysis tasks.
Template Attack and Machine Learning: Template attack is a well-known side-channel analysis technique that uses statistical models to estimate the leakage of sensitive information. By combining machine learning algorithms with template attacks, researchers have been able to enhance the efficiency and effectiveness of side-channel analysis. Machine learning models can be trained to predict the leakage patterns, leading to improved key recovery or detection of vulnerable cryptographic implementations.
Adversarial Machine Learning: Adversarial machine learning has been explored to assess and improve the robustness of side-channel countermeasures. Adversarial attacks aim to find weaknesses or vulnerabilities in side-channel countermeasures by attempting to bypass them. By studying adversarial attacks, researchers can enhance the resilience of countermeasures and design more secure implementations.
Transfer Learning and Domain Adaptation: Transfer learning and domain adaptation techniques have been employed to address the challenge of limited side-channel data. These methods allow leveraging knowledge and models trained on one dataset or system to improve analysis on a different but related dataset or system. By transferring knowledge and adapting models, side-channel analysis can be performed more effectively with smaller or diverse datasets.
Deep Generative Models: Deep generative models, such as variational autoencoders (VAEs) and generative adversarial networks (GANs), have been applied to side-channel analysis tasks. These models can learn the underlying distribution of side-channel data and generate synthetic side-channel traces. Deep generative models enable data augmentation, the creation of new training samples, and the exploration of novel side-channel leakage scenarios.
Multi-Modal Analysis: Deep learning techniques have facilitated multi-modal analysis, which involves combining information from multiple side channels to enhance attacks or countermeasures. By leveraging multiple sources of side-channel information, such as power consumption and electromagnetic radiation, deep learning models can capture richer representations and improve the accuracy of side-channel analysis.
The development of deep learning and AI methods has opened up new possibilities for side-channel analysis, allowing for more accurate, efficient, and robust attacks and countermeasures. These advancements have contributed to advancing the state-of-the-art in side-channel analysis and enhancing the security of cryptographic implementations. However, it’s worth noting that as AI methods evolve, so do potential adversarial attacks and the need for ongoing research to stay ahead of emerging threats.